|
|
|
help...need info on this log
|
|
|
mesa101
Member

|
20. January 2006 @ 13:24 |
 Link to this message
Link to this message

|
what is domain hijack? do i need to remove?
Logfile of HijackThis v1.99.1
Scan saved at 6:22:09 PM, on 1/20/2006
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180)
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\csrss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
c:\program files\mcafee.com\agent\mcdetect.exe
c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
C:\Program Files\Spyware Doctor\sdhelp.exe
C:\WINDOWS\system32\wdfmgr.exe
C:\WINDOWS\system32\ZoneLabs\vsmon.exe
c:\PROGRA~1\mcafee.com\vso\mcshield.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\VTTimer.exe
C:\Program Files\QuickTime\qttask.exe
C:\WINDOWS\zHotkey.exe
C:\Program Files\Digital Media Reader\shwiconem.exe
C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
C:\PROGRA~1\mcafee.com\vso\mcvsshld.exe
C:\PROGRA~1\mcafee.com\agent\mcagent.exe
C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
C:\Program Files\Spyware Doctor\swdoctor.exe
c:\progra~1\mcafee.com\vso\mcvsescn.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\DOCUME~1\Owner\LOCALS~1\Temp\Temporary Directory 1 for hijackthis[1].zip\HijackThis.exe
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.gatewaybiz.com
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant =
O2 - BHO: AcroIEHlprObj Class - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 6.0\Reader\ActiveX\AcroIEHelper.dll
O2 - BHO: (no name) - {549B5CA7-4A86-11D7-A4DF-000874180BB3} - (no file)
O2 - BHO: PCTools Site Guard - {5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB} - C:\PROGRA~1\SPYWAR~1\tools\iesdsg.dll
O2 - BHO: PCTools Browser Monitor - {B56A7D7D-6927-48C8-A975-17DF180C71AC} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O2 - BHO: (no name) - {FDD3B846-8D59-4ffb-8758-209B6AD74ACC} - (no file)
O3 - Toolbar: McAfee VirusScan - {BA52B914-B692-46c4-B683-905236F6F655} - c:\progra~1\mcafee.com\vso\mcvsshl.dll
O4 - HKLM\..\Run: [VTTimer] VTTimer.exe
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKLM\..\Run: [CHotkey] zHotkey.exe
O4 - HKLM\..\Run: [SunKistEM] C:\Program Files\Digital Media Reader\shwiconem.exe
O4 - HKLM\..\Run: [SunJavaUpdateSched] C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
O4 - HKLM\..\Run: [Zone Labs Client] C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
O4 - HKLM\..\Run: [Microsoft Works Update Detection] C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
O4 - HKLM\..\Run: [VSOCheckTask] "c:\PROGRA~1\mcafee.com\vso\mcmnhdlr.exe" /checktask
O4 - HKLM\..\Run: [VirusScan Online] "c:\PROGRA~1\mcafee.com\vso\mcvsshld.exe"
O4 - HKLM\..\Run: [MCAgentExe] c:\PROGRA~1\mcafee.com\agent\mcagent.exe
O4 - HKLM\..\Run: [MCUpdateExe] c:\PROGRA~1\mcafee.com\agent\mcupdate.exe
O4 - HKLM\..\Run: [AnyDVD] C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
O4 - HKLM\..\Run: [NeroFilterCheck] C:\WINDOWS\system32\NeroCheck.exe
O4 - HKLM\..\Run: [Recguard] C:\WINDOWS\SMINST\RECGUARD.EXE
O4 - HKCU\..\Run: [MSMSGS] "C:\Program Files\Messenger\msmsgs.exe" /background
O4 - HKCU\..\Run: [Spyware Doctor] "C:\Program Files\Spyware Doctor\swdoctor.exe" /Q
O9 - Extra button: Spyware Doctor - {2D663D1A-8670-49D9-A1A5-4C56B4E14E84} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O17 - HKLM\System\CCS\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O17 - HKLM\System\CS1\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O18 - Filter: text/html - (no CLSID) - (no file)
O23 - Service: McAfee WSC Integration (McDetect.exe) - McAfee, Inc - c:\program files\mcafee.com\agent\mcdetect.exe
O23 - Service: McAfee.com McShield (McShield) - Unknown owner - c:\PROGRA~1\mcafee.com\vso\mcshield.exe
O23 - Service: McAfee Task Scheduler (McTskshd.exe) - McAfee, Inc - c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
O23 - Service: McAfee SecurityCenter Update Manager (mcupdmgr.exe) - McAfee, Inc - C:\PROGRA~1\McAfee.com\Agent\mcupdmgr.exe
O23 - Service: McAfee.com VirusScan Online Realtime Engine (MCVSRte) - McAfee, Inc - c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
O23 - Service: PrismXL - New Boundary Technologies, Inc. - C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
O23 - Service: PC Tools Spyware Doctor (SDhelper) - PC Tools - C:\Program Files\Spyware Doctor\sdhelp.exe
O23 - Service: TrueVector Internet Monitor (vsmon) - Zone Labs, LLC - C:\WINDOWS\system32\ZoneLabs\vsmon.exe
|
|
Advertisement

|
  |
|
|
Member

|
21. January 2006 @ 12:34 |
 Link to this message
Link to this message

|
Unzip Hijack This from the zip folder, then use Hijack This.
Quote:
what is domain hijack?
Certain browser hijackers take control of your browser (in this case - Internet Explorer) and redirect you to a site they own. Certain examples: lop.com and coolwebsearch do this to get profits. Suggestion: Use a safer browser such as FireFox and/or Avant.
Place a checkmark by this and remove:
R0 - HKLM\Software\Microsoft\Internet Explorer\Search,SearchAssistant =
O2 - BHO: (no name) - {549B5CA7-4A86-11D7-A4DF-000874180BB3} - (no file)
O2 - BHO: (no name) - {FDD3B846-8D59-4ffb-8758-209B6AD74ACC} - (no file)
O17 - HKLM\System\CCS\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O17 - HKLM\System\CS1\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O18 - Filter: text/html - (no CLSID) - (no file)
Download and run this utility:
http://www.trendmicro.com/cwshredder/

 - Ideal way to deal with the MPAA~RIAA |
|
mesa101
Member

|
21. January 2006 @ 13:49 |
 Link to this message
Link to this message

|
|
the 2 items 017 are these my internet connections?...they are not there when im not connected?..the others i removed..i just want to be sure about the other 2
|
Member

|
21. January 2006 @ 13:53 |
 Link to this message
Link to this message

|
|
Your host file has been hijacked to site(s) owned by lop.com . Normally, there should be a standard IP address there for authentication purposes only, but some malware/adware add their IP address so that every time you use IE (or some other browser), you would be redirected over there, even if you typed a different url address...
The author of Hijack This indicates that an entry in the 017 spot are entries indicating the presence of lop.com sites.

 - Ideal way to deal with the MPAA~RIAA This message has been edited since posting. Last time this message was edited on 21. January 2006 @ 13:55
|
|
mesa101
Member

|
21. January 2006 @ 15:43 |
 Link to this message
Link to this message

|
|
ok. thanks i will delete those too.
|
|
mesa101
Member

|
21. January 2006 @ 15:46 |
 Link to this message
Link to this message

|
|
i deleted those 017 files but when i restart my computer and rescan they are back again?...what do i need to do?
|
Member

|
21. January 2006 @ 19:19 |
 Link to this message
Link to this message

|
|
Boot into safe mode and delete from there. Reboot, then post another hijack this log...

 - Ideal way to deal with the MPAA~RIAA |
|
mesa101
Member

|
21. January 2006 @ 19:41 |
 Link to this message
Link to this message

|
i did as you said but it appears the 017 entry is still there...if i scan when im not connected it's not there but when im connected it's there. below is the results.
Logfile of HijackThis v1.99.1
Scan saved at 12:39:39 AM, on 1/22/2006
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180)
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\csrss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\VTTimer.exe
C:\WINDOWS\zHotkey.exe
C:\Program Files\Digital Media Reader\shwiconem.exe
C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
C:\PROGRA~1\mcafee.com\vso\mcvsshld.exe
C:\PROGRA~1\mcafee.com\agent\mcagent.exe
c:\progra~1\mcafee.com\vso\mcvsescn.exe
C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
C:\Program Files\Spyware Doctor\swdoctor.exe
c:\program files\mcafee.com\agent\mcdetect.exe
c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
C:\Program Files\Spyware Doctor\sdhelp.exe
C:\WINDOWS\system32\wdfmgr.exe
C:\WINDOWS\system32\ZoneLabs\vsmon.exe
c:\PROGRA~1\mcafee.com\vso\mcshield.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\system32\wuauclt.exe
C:\Program Files\HijackThis.exe
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.gatewaybiz.com
O2 - BHO: AcroIEHlprObj Class - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 6.0\Reader\ActiveX\AcroIEHelper.dll
O2 - BHO: PCTools Site Guard - {5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB} - C:\PROGRA~1\SPYWAR~1\tools\iesdsg.dll
O2 - BHO: PCTools Browser Monitor - {B56A7D7D-6927-48C8-A975-17DF180C71AC} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O3 - Toolbar: McAfee VirusScan - {BA52B914-B692-46c4-B683-905236F6F655} - c:\progra~1\mcafee.com\vso\mcvsshl.dll
O4 - HKLM\..\Run: [VTTimer] VTTimer.exe
O4 - HKLM\..\Run: [CHotkey] zHotkey.exe
O4 - HKLM\..\Run: [SunKistEM] C:\Program Files\Digital Media Reader\shwiconem.exe
O4 - HKLM\..\Run: [SunJavaUpdateSched] C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
O4 - HKLM\..\Run: [Zone Labs Client] C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
O4 - HKLM\..\Run: [Microsoft Works Update Detection] C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
O4 - HKLM\..\Run: [VSOCheckTask] "c:\PROGRA~1\mcafee.com\vso\mcmnhdlr.exe" /checktask
O4 - HKLM\..\Run: [VirusScan Online] "c:\PROGRA~1\mcafee.com\vso\mcvsshld.exe"
O4 - HKLM\..\Run: [MCAgentExe] c:\PROGRA~1\mcafee.com\agent\mcagent.exe
O4 - HKLM\..\Run: [MCUpdateExe] C:\PROGRA~1\mcafee.com\agent\mcupdate.exe
O4 - HKLM\..\Run: [AnyDVD] C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
O4 - HKLM\..\Run: [NeroFilterCheck] C:\WINDOWS\system32\NeroCheck.exe
O4 - HKLM\..\Run: [Recguard] C:\WINDOWS\SMINST\RECGUARD.EXE
O4 - HKCU\..\Run: [MSMSGS] "C:\Program Files\Messenger\msmsgs.exe" /background
O4 - HKCU\..\Run: [Spyware Doctor] "C:\Program Files\Spyware Doctor\swdoctor.exe" /Q
O9 - Extra button: Spyware Doctor - {2D663D1A-8670-49D9-A1A5-4C56B4E14E84} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O17 - HKLM\System\CCS\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O17 - HKLM\System\CS1\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O23 - Service: McAfee WSC Integration (McDetect.exe) - McAfee, Inc - c:\program files\mcafee.com\agent\mcdetect.exe
O23 - Service: McAfee.com McShield (McShield) - Unknown owner - c:\PROGRA~1\mcafee.com\vso\mcshield.exe
O23 - Service: McAfee Task Scheduler (McTskshd.exe) - McAfee, Inc - c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
O23 - Service: McAfee SecurityCenter Update Manager (mcupdmgr.exe) - McAfee, Inc - C:\PROGRA~1\McAfee.com\Agent\mcupdmgr.exe
O23 - Service: McAfee.com VirusScan Online Realtime Engine (MCVSRte) - McAfee, Inc - c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
O23 - Service: PrismXL - New Boundary Technologies, Inc. - C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
O23 - Service: PC Tools Spyware Doctor (SDhelper) - PC Tools Research Pty Ltd - C:\Program Files\Spyware Doctor\sdhelp.exe
O23 - Service: TrueVector Internet Monitor (vsmon) - Zone Labs, LLC - C:\WINDOWS\system32\ZoneLabs\vsmon.exe
|
Member

|
21. January 2006 @ 23:42 |
 Link to this message
Link to this message

|

 - Ideal way to deal with the MPAA~RIAA |
|
mesa101
Member

|
22. January 2006 @ 04:34 |
 Link to this message
Link to this message

|
|
i use spyware doctor {pay version }. it found nothing
|
Member

|
22. January 2006 @ 11:41 |
 Link to this message
Link to this message

|
Ok, let's try this method, shall we?
If you have download and installed Spybot: Search and Destroy, go ahead and use it.
If you've never used, or are unfamiliar with it, I'll include some screen shots to guide you.
Open up Spybot and you'll get this:
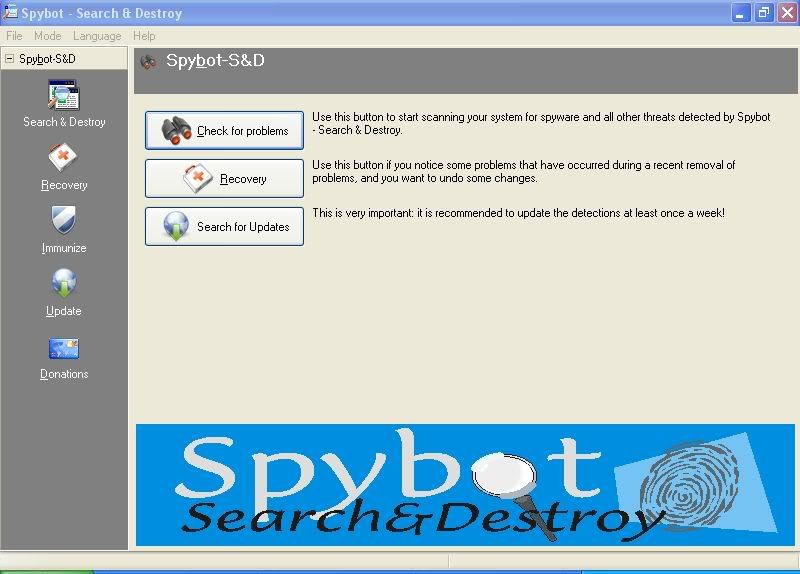
On the top left, click Mode, scroll down to select Advanced mode:

A message will pop up warning you that the advanced mode contains more features and that it could also harm your system. Select Yes:
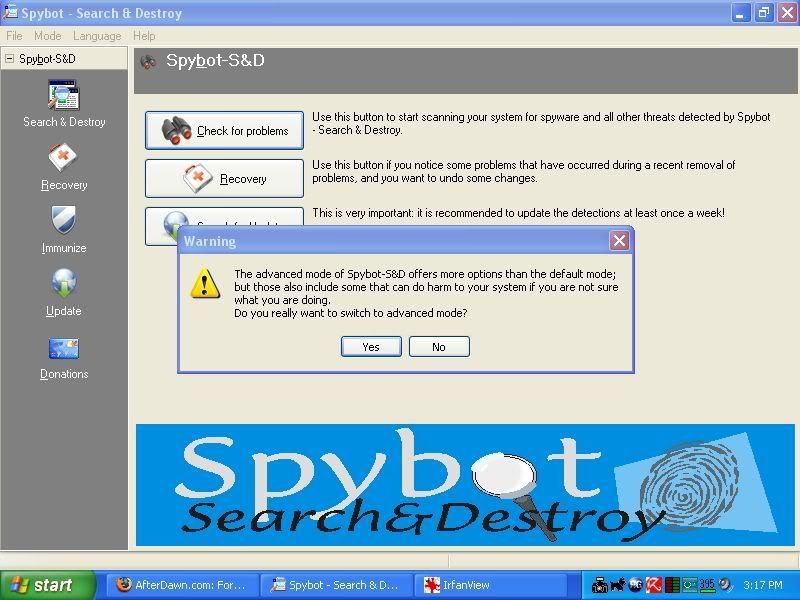
You'll notice, after you have clicked Yes, on the bottom left, this will appear:
Move your mouse to Tools:
After clicking Tools, you'll get something similar to this:
The check marks on certain items may be different than yours due to the fact that yours is still at default settings whereas I had fiddled the settings in the past, so mine may look different than yours.
Now, in the white area with all the check marked items, make sure Host File is check marked. If not, go ahead and do so now:
After the check mark on Host File, the left side will include a button Host File for you to click on:
Go ahead and click it...
Now, in the white area, there should only be 1 entry. Under Host, it should read localhost and under Destination address, it should read 127.0.0.1 (or something close to that)...
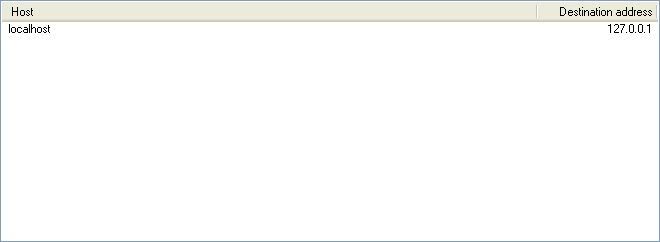
Now, look for the same entries that were indicated with Hijack This, the ones located with the entry 017. Select the ones that shouldn't be there, and choose "Remove selected entries." Remember, do not delete the entry, localhost: 127.0.0.1
After the deletions, post another hijack this log.

 - Ideal way to deal with the MPAA~RIAA This message has been edited since posting. Last time this message was edited on 22. January 2006 @ 11:44
|
|
mesa101
Member

|
22. January 2006 @ 15:25 |
 Link to this message
Link to this message

|
i did everything as you said...the only thing that appeard in Spybot was local host...
Logfile of HijackThis v1.99.1
Scan saved at 8:25:18 PM, on 1/22/2006
Platform: Windows XP SP2 (WinNT 5.01.2600)
MSIE: Internet Explorer v6.00 SP2 (6.00.2900.2180)
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\csrss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\system32\spoolsv.exe
c:\program files\mcafee.com\agent\mcdetect.exe
c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
C:\Program Files\Spyware Doctor\sdhelp.exe
C:\WINDOWS\system32\wdfmgr.exe
C:\WINDOWS\system32\ZoneLabs\vsmon.exe
c:\PROGRA~1\mcafee.com\vso\mcshield.exe
C:\WINDOWS\System32\alg.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\VTTimer.exe
C:\WINDOWS\zHotkey.exe
C:\Program Files\Digital Media Reader\shwiconem.exe
C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
C:\PROGRA~1\mcafee.com\vso\mcvsshld.exe
C:\PROGRA~1\mcafee.com\agent\mcagent.exe
C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
c:\progra~1\mcafee.com\vso\mcvsescn.exe
C:\Program Files\Spyware Doctor\swdoctor.exe
C:\Program Files\Internet Explorer\iexplore.exe
C:\Program Files\HijackThis.exe
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.gatewaybiz.com
O2 - BHO: AcroIEHlprObj Class - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Adobe\Acrobat 6.0\Reader\ActiveX\AcroIEHelper.dll
O2 - BHO: (no name) - {53707962-6F74-2D53-2644-206D7942484F} - C:\PROGRA~1\SPYBOT~1\SDHelper.dll
O2 - BHO: PCTools Site Guard - {5C8B2A36-3DB1-42A4-A3CB-D426709BBFEB} - C:\PROGRA~1\SPYWAR~1\tools\iesdsg.dll
O2 - BHO: PCTools Browser Monitor - {B56A7D7D-6927-48C8-A975-17DF180C71AC} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O3 - Toolbar: McAfee VirusScan - {BA52B914-B692-46c4-B683-905236F6F655} - c:\progra~1\mcafee.com\vso\mcvsshl.dll
O4 - HKLM\..\Run: [VTTimer] VTTimer.exe
O4 - HKLM\..\Run: [CHotkey] zHotkey.exe
O4 - HKLM\..\Run: [SunKistEM] C:\Program Files\Digital Media Reader\shwiconem.exe
O4 - HKLM\..\Run: [SunJavaUpdateSched] C:\Program Files\Java\jre1.5.0_05\bin\jusched.exe
O4 - HKLM\..\Run: [Zone Labs Client] C:\Program Files\Zone Labs\ZoneAlarm\zlclient.exe
O4 - HKLM\..\Run: [Microsoft Works Update Detection] C:\Program Files\Common Files\Microsoft Shared\Works Shared\WkUFind.exe
O4 - HKLM\..\Run: [VSOCheckTask] "c:\PROGRA~1\mcafee.com\vso\mcmnhdlr.exe" /checktask
O4 - HKLM\..\Run: [VirusScan Online] "c:\PROGRA~1\mcafee.com\vso\mcvsshld.exe"
O4 - HKLM\..\Run: [MCAgentExe] c:\PROGRA~1\mcafee.com\agent\mcagent.exe
O4 - HKLM\..\Run: [MCUpdateExe] C:\PROGRA~1\mcafee.com\agent\mcupdate.exe
O4 - HKLM\..\Run: [AnyDVD] C:\Program Files\SlySoft\AnyDVD\AnyDVD.exe
O4 - HKLM\..\Run: [NeroFilterCheck] C:\WINDOWS\system32\NeroCheck.exe
O4 - HKLM\..\Run: [Recguard] C:\WINDOWS\SMINST\RECGUARD.EXE
O4 - HKCU\..\Run: [MSMSGS] "C:\Program Files\Messenger\msmsgs.exe" /background
O4 - HKCU\..\Run: [Spyware Doctor] "C:\Program Files\Spyware Doctor\swdoctor.exe" /Q
O9 - Extra button: Spyware Doctor - {2D663D1A-8670-49D9-A1A5-4C56B4E14E84} - C:\PROGRA~1\SPYWAR~1\tools\iesdpb.dll
O17 - HKLM\System\CCS\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O17 - HKLM\System\CS1\Services\Tcpip\..\{0FE6EC35-FD78-4B28-B3C5-8FBC73F8FA8F}: NameServer = 66.110.205.10 66.110.205.75
O23 - Service: McAfee WSC Integration (McDetect.exe) - McAfee, Inc - c:\program files\mcafee.com\agent\mcdetect.exe
O23 - Service: McAfee.com McShield (McShield) - Unknown owner - c:\PROGRA~1\mcafee.com\vso\mcshield.exe
O23 - Service: McAfee Task Scheduler (McTskshd.exe) - McAfee, Inc - c:\PROGRA~1\mcafee.com\agent\mctskshd.exe
O23 - Service: McAfee SecurityCenter Update Manager (mcupdmgr.exe) - McAfee, Inc - C:\PROGRA~1\McAfee.com\Agent\mcupdmgr.exe
O23 - Service: McAfee.com VirusScan Online Realtime Engine (MCVSRte) - McAfee, Inc - c:\PROGRA~1\mcafee.com\vso\mcvsrte.exe
O23 - Service: PrismXL - New Boundary Technologies, Inc. - C:\Program Files\Common Files\New Boundary\PrismXL\PRISMXL.SYS
O23 - Service: PC Tools Spyware Doctor (SDhelper) - PC Tools Research Pty Ltd - C:\Program Files\Spyware Doctor\sdhelp.exe
O23 - Service: TrueVector Internet Monitor (vsmon) - Zone Labs, LLC - C:\WINDOWS\system32\ZoneLabs\vsmon.exe
|
Member

|
22. January 2006 @ 15:46 |
 Link to this message
Link to this message

|
|
If you have Microsoft Antispyware, go ahead and open it. Make sure you have the latest updates. If not, go to File, choose Check for updates.... After the updates:
On the right side, click on Advanced Tools. Then under System Tools, choose System Explorers (the icon with the person in front of the monitor). Now something should appear on the left side. Under Networking, choose Windows Hosts File. Look for the ones that do not belong there and choose Permanently Remove Host. The only that should be there is localhost.
Reboot your comp after the removal. After rebooting, run another hijack this scan. If it's still there, it could mean that most likely System Restore kept a copy of your computer state.
Let me know if it's still there or not.

 - Ideal way to deal with the MPAA~RIAA This message has been edited since posting. Last time this message was edited on 22. January 2006 @ 15:47
|
|
mesa101
Member

|
22. January 2006 @ 17:04 |
 Link to this message
Link to this message

|
let's see...i installed microsoft spyware updated did the scan..it found a few things spyware doctor and Spybot didnt..under hosts all it had was the local host.?...017 still there...what am i gonna have to do reformat?
|
Member

|
23. January 2006 @ 19:41 |
 Link to this message
Link to this message

|
|
Really shouldn't have to. This is strange that those entries in your host file still exist after removing them. I think it's best to use every anti-spyware app under safe mode, using full system scan. The lop.com hijacking should be easy to remove, but it seems they have improved on their techniques. I'll look for more info on this matter, so that this is gone once and for all...

 - Ideal way to deal with the MPAA~RIAA |
Member

|
31. January 2006 @ 22:03 |
 Link to this message
Link to this message

|
|
You could disabling System Restore temporarily, then boot into safe mode, then run Hijack This, then delete those entries, then restart your comp, enable System Restore...see how that turns out...

 - Ideal way to deal with the MPAA~RIAA |
|
spertti
Senior Member

|
1. February 2006 @ 12:36 |
 Link to this message
Link to this message

|
|
I don´t really see a problem with those 017 lines. If you live in United States [City: Vienna, Georgia] leave those lines as they are. In worst case you´ll lose your internet connection.
|
|
mesa101
Member

|
1. February 2006 @ 12:47 |
 Link to this message
Link to this message

|
|
i figured they might have to do with my server or connection..vienna is about 30 miles from here...i live in leslie ga....i will leave them as they are.. thanks for the help
|
|
spertti
Senior Member

|
1. February 2006 @ 12:50 |
 Link to this message
Link to this message

|
|
Nothing =) You tried really hard to lose your connection but fortunately you didn´t succeed =)
|
|
mesa101
Member

|
1. February 2006 @ 13:25 |
 Link to this message
Link to this message

|
|
hehehe,, im good at messing stuff up....i couldn't live without the internet though...food maybe - internet no!!
|
|
Advertisement

|
  |
|
|
spertti
Senior Member

|
1. February 2006 @ 13:29 |
 Link to this message
Link to this message

|
|
That´s the attitude we´re looking for =) Who needs to eat....
|
|


